|
(a) What are the major functions of a
CPU? [1]
FETCH/EXECUTE - READ/WRITE [1]
Award credit for valid answers expressed differently.
(b) For these two assembly instructions:
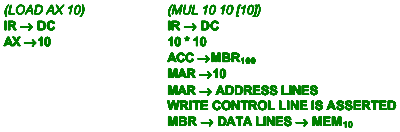
LOAD AX, 10
MUL 10, 10, [10]
(i) State the instruction format clearly indicating the Opcode and
the Operand. [2]
LOAD (OPCODE) AX(OPERAND1)
10(OPERAND2) 2-ADDRESS [1]
MUL(OPCODE) 10(OPERAND1) 10(OPERAND2)
10(OPERAND3) 3-ADDRESS
(ii) Write the steps of the execute-cycle for each of the above instructions.
[5]
[5] for fully correct answers; deducting
[1] for each defect, down to
[2] for generally the right ideas, and [1] over all for some hint
of
something right.
(c) The following sequence of opcode instructions has been produced
to use a stack to evaluate an expression.
PUSH 10
PUSH 10
PUSH 2
PUSH 2
MUL
ADD
PUSH 3
PUSH 3
ADD
ADD
SUB
POP A
(i) What is the expression being evaluated? [1]
A = ( 10 - ( 10 + 2 * 2 ) + ( 3 + 3 ) ) )
[1]
(ii) What is the final result of the evaluated expression? [1]
A = 10 [1]
(iii) What is the required stack depth to evaluate this expression?
[1]
STACK DEPTH = 4 Students must show workings
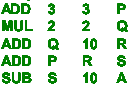
(iv) Rewrite the above sequence of instructions to compute the same
expression,
using a 3-address instruction format. [3]
[3] for a fully-correct program (not necessarily
this one);
[2] if there is a single defect;
[1] if it has some of the right ideas but is seriously flawed.
(d) Identify the Bit-stream encoded on
each of the following digital signatures: [3]
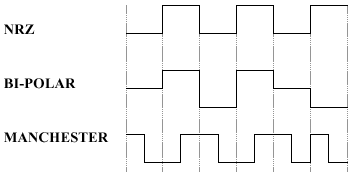
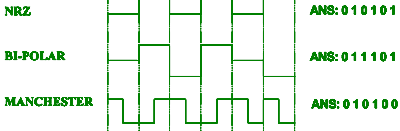
[1]
for each fully-correct answer.
(e) Considering what happens when a program
is running, what is the main difference between main memory and secondary-memory?
[2]
Main memory only holds the active portions
of a program [1] whilst
secondary memory keeps those not in continual use. [1]
(f) What is the characteristic that determines the difference in the
time taken to retrieve data using a Random-access method, when compared
to a Direct-access method? [2]
'Location Dependency' [1] (with explanation
[1])
(g) A typical computer system displays several layers of memory, based
on the diagram below:
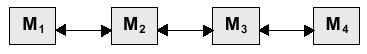
(i) Identify the different levels of
memory, assuming that M1 is the fastest form of
memory. [2]
M1 = CPU REGISTERS, M2 = CACHE,
M3 = MAIN MEMORY, M4 = SECONDARY MEMORY
[2] for fully correct; [1] for two or three correct.
(ii) Identify the unit of transfer between the memory categories.
[2]
M1 M2
= a word, M2 M2
= a word, M2 M3
= A block of words, M3
= A block of words,
M3 M4
= A page M4
= A page
[2] for fully correct; [1] for two out of three.
(h) Many of today's organisations’ large LAN topologies such
as Bus, Star, Tree, etc. are no longer single architectures. Rather,
many of these topologies are multi-configurational, meaning that they
combine two network topologies together as one. One such combination
is Bus/Star.
(i) Illustrate what such a network would look like. [1]
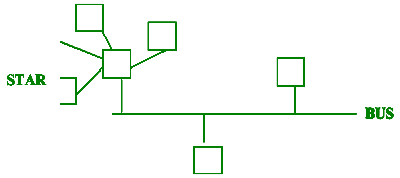
(These or other valid points; one mark each
if explained. If explanations
are too brief, give only up to [2] over all. These are inclusive of
the
advantages/disadvantages of BUS & STAR)
(ii) Describe two advantages and two disadvantages of this network.
[4]
Easy to add nodes
More than one central controller
Limited bandwidth
Resources are limited
|





